Table of Contents
- 1 The Moment of Truth
- 2 Why Nobody Had Done This Before
- 3 The Deep Dive Begins
- 4 The First Breakthrough
- 5 Platform-Specific Nightmares
- 6 The Compilation Ballet
- 7 The Security Rabbit Hole
- 8 The CI/CD Nightmare
- 9 The Release Process Revolution
- 10 The First Success
- 11 The Ripple Effect
- 12 The Unexpected Challenges
- 13 Looking Back
Notice: While native extensions for rdkafka have been extensively tested and are no longer experimental, they may not work in all environments or configurations. If you find any issues with the precompiled extensions, please report them immediately and they will be resolved.
Every Ruby developer knows this excruciating feeling: you're setting up a project, running bundle install, and then... you wait. And wait. And wait some more as rdkafka compiles for what feels like eternity. Sixty to ninety seconds of pure frustration, staring at a seemingly frozen terminal that gives no indication of progress while your coffee is getting cold.
I've been there countless times. As the maintainer of the Karafka ecosystem, I've watched developers struggle with this for years. The rdkafka gem - essential for Apache Kafka integration in Ruby - was notorious for its painfully slow installation. Docker builds took forever. CI pipelines crawled. New developers gave up before they even started. Not to mention the countless compilation crashes that were nearly impossible to debug.
Something had to change.
The Moment of Truth
It was during a particularly frustrating debugging session that I realized the real scope of the problem. I was helping a developer who couldn't get rdkafka to install on his macOS dev machine. Build tools missing. Compilation failing. Dependencies conflicting. The usual nightmare.
As I walked him through the solution for the hundredth time, I did some quick math. The rdkafka gem gets downloaded over a million times per month. Each installation takes about 60 seconds to compile. That's 60 million seconds of CPU time every month - nearly two years of continuous processing power wasted on compilation alone.
But the real kicker? All those installations were essentially building the same thing over and over again. The same librdkafka library. The same OpenSSL. The same compression libraries. Millions of identical compilations happening across the world, burning through CPU cycles and developer patience.
That's when I decided to solve this once and for all.
Why Nobody Had Done This Before
You might wonder: if this was such an obvious problem, why hadn't anyone solved it already? The answer lies in what I call "compatibility hell."
Unlike many other Ruby gems that might need basic compilation, rdkafka is a complex beast. It wraps librdkafka, a sophisticated C library that depends on a web of other libraries:
- OpenSSL for encryption
- Cyrus SASL for authentication
- MIT Kerberos for enterprise security
- Multiple compression libraries (zlib, zstd, lz4, snappy)
- System libraries that vary wildly across platforms
Every Linux distribution has slightly different versions of these libraries. Ubuntu uses one version of OpenSSL, CentOS uses another. Alpine Linux uses musl instead of glibc. macOS has its own quirks. Creating a single binary that works everywhere seemed impossible.
My previous attempts had failed, because they tried to link against system libraries dynamically. This works great... until you deploy to a system with different library versions. Then everything breaks spectacularly.
The Deep Dive Begins
I started by studying how other Ruby gems had tackled similar problems. The nokogiri gem had become the gold standard for this approach - they'd successfully shipped precompiled binaries that eliminated the notorious compilation headaches that had plagued XML processing in Ruby for years. Their success proved that it was possible.
Other ecosystems had figured this out years ago. Python has wheels. Go has static binaries. Rust has excellent cross-compilation. While Ruby has improved with precompiled gems for many platforms, the ecosystem still feels inconsistent - you never know if you'll get a precompiled gem or need to compile from source. The solution, I realized, was static linking. Instead of depending on system libraries, I would bundle everything into self-contained binaries.
Every dependency would be compiled from source and linked statically into the final library.
Sounds simple, right? It wasn't.
The First Breakthrough
My first success came with the Linux x86_64 GNU systems - your typical Ubuntu or CentOS server. After days of tweaking the compiler flags and build scripts, I had a working prototype. The binary was larger than the dynamically linked version, but it worked anywhere.
The installation time dropped from 60+ seconds to under 5 seconds!
But then I tried it on Alpine Linux. Complete failure. Alpine uses musl libc instead of glibc, and my carefully crafted build didn't work at all.
Platform-Specific Nightmares
Each platform brought its own specific challenges:
-
Alpine Linux (musl): Different system calls, different library conventions, different compiler behavior. I had to rebuild the entire toolchain with the musl-specific flags. The Cyrus SASL library was particularly troublesome - it kept trying to use glibc-specific functions that didn't exist in musl.
-
macOS ARM64: Apple Silicon Macs use a completely different architecture. The build system had to use different SDK paths, and handle Apple's unique library linking requirements. Plus, macOS has its own ideas about where libraries should live.
-
Security concerns: Precompiled binaries are inherently less trustworthy than source code. How do you prove that a binary contains exactly what it claims to contain? I implemented the SHA256 verification for every dependency, but that was just the beginning.
The Compilation Ballet
Building a single native extension became an intricate dance of dependencies. Each library had to be compiled in the correct order, with the right flags, targeting the right architecture. One mistake and the entire build would fail.
I developed a common build system that could handle all platforms:
# Download and verify every dependency
secure_download "$(get_openssl_url)" "$OPENSSL_TARBALL"
verify_checksum "$OPENSSL_TARBALL"
# Build in the correct order
build_openssl_for_platform "$PLATFORM"
build_kerberos_for_platform "$PLATFORM"
build_sasl_for_platform "$PLATFORM"
# ... and so onThe build scripts grew to over 2,000 lines of carefully crafted shell code. Every platform had its own nuances, its own gotchas, its own way of making my life difficult.
The Security Rabbit Hole
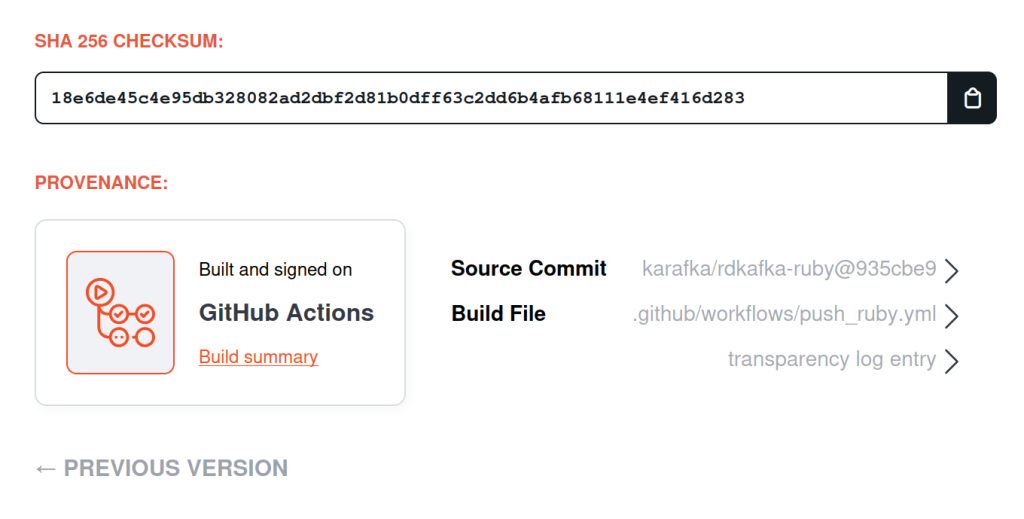
Precompiled binaries introduce a fundamental security challenge: trust. When you compile from source, you can theoretically inspect every line of code. With precompiled binaries, you're trusting that the binary contains exactly what it claims to contain.
I spent weeks, implementing a comprehensive security model consisting of:
- SHA256 verification for every downloaded dependency
- Cryptographic attestation through RubyGems Trusted Publishing
- Reproducible builds with the pinned versions
- Supply chain protection against malicious dependencies
The build logs became a security audit trail:
[SECURITY] Verifying checksum for openssl-3.0.16.tar.gz...
[SECURITY] ✅ Checksum verified for openssl-3.0.16.tar.gz
[SECURITY] 🔒 SECURITY VERIFICATION COMPLETEThe CI/CD Nightmare
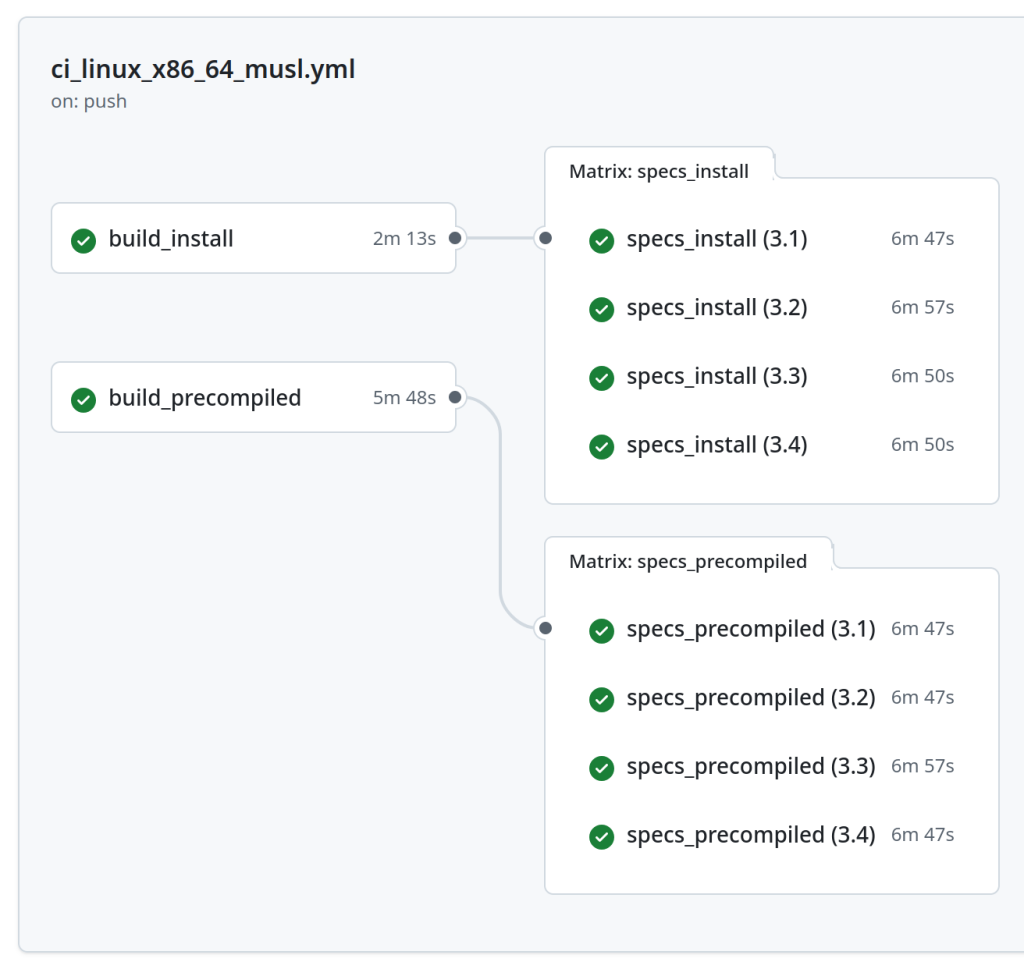
Testing native extensions across multiple platforms and Ruby versions created a combinatorial explosion of complexity. My GitHub Actions configuration grew from a simple test matrix to a multi-stage pipeline with separate build and test phases.
Each platform needed its own runners:
- Linux builds ran on Ubuntu with Docker containers
- macOS builds ran on actual macOS runners
- Each build had to be tested across Ruby
3.1,3.2,3.3,3.4, and3.5
The CI pipeline became a carefully choreographed dance of builds, tests, and releases. One failure anywhere would cascade through the entire system.
Each platform requires 10 separate CI actions - from compilation to testing across Ruby versions. Multiplied across all supported platforms, this creates a complex 30-action pipeline.
The Release Process Revolution
Publishing native extensions isn't just gem push. Each release now involves building on multiple platforms simultaneously, testing each binary across Ruby versions, and coordinating the release of multiple platform-specific gems.
I implemented RubyGems Trusted Publishing, which uses cryptographic tokens instead of API keys. This meant rebuilding the entire release process from scratch, but it provided better security and audit trails.
The First Success
After months of work, I finally had working native extensions for all three major platforms. The moment of truth came, when I installed the gem for the first time using the precompiled binary:
$ gem install rdkafka
Successfully installed rdkafka-0.22.0-x86_64-linux-gnu
1 gem installedI sat there staring at my terminal, hardly believing it had worked. Months of frustration, debugging, and near misses had led to this moment. Three seconds instead of sixty!
The Ripple Effect
The impact is beyond just faster installations. The Docker builds that previously had taken several minutes, now completed much faster. The CI pipelines that developers had learned to ignore suddenly became responsive. New contributors could set up the development environments without fighting the compiler errors.
But the numbers that really struck me were the environmental ones. With over a million downloads per month, those 60 seconds of compilation time added up to 60 million seconds of CPU usage monthly. That's 16,667 hours of processing power - and all the associated energy consumption and CO2 emissions.
The Unexpected Challenges
Just when I thought I was done, new challenges emerged. Some users needed to stick with source compilation for custom configurations. Others wanted to verify that the precompiled binaries were truly equivalent to the source builds.
I added fallback mechanisms and comprehensive documentation. You can still force source compilation if needed:
gem 'rdkafka', force_ruby_platform: trueBut for most users, the native extensions work transparently. Install the gem, and you automatically get the fastest experience possible.
Looking Back
This project has taught me, that sometimes the most valuable improvements are the ones that the users never notice. Nobody celebrates faster gem installation. There are no awards for reducing the compilation time. But those small improvements compound into something much larger.
Every developer who doesn't wait for rdkafka to compile can focus on building something amazing instead. Every CI pipeline that completes faster means more iterations, more experiments, more innovation.
The 60-second problem is solved. It took months of engineering effort, thousands of lines of code, and more debugging sessions than I care to count. But now, when you run gem install rdkafka or bundle install, it just works.
Fast.
The rdkafka and karafka-rdkafka gems with native extensions are available now. Your next bundle install will be faster than ever. For complete documentation, visit the Karafka documentation.